Some say big data is a threat, while others consider it a saviour. At TELUS, we want to be transparent with our business operations. We want you with us, every step of the way into bettering our next generation. In this technology-driven economy, it is extremely important for us to understand the risks we all take when creating our online presence. To do so, we need to open up about the implications of holding large amounts of data online.
Opportunities with Big Data and TELUS
Our mission at TELUS is to “enable our customers and team members to do what they want easily.” (TELUS, 2018). Operating in the telecommunications industry holds large potential for success. Big data provides a better picture to what you want, and how we can change to help you achieve full efficiency in your everyday lives.
Keeping track of how much each family spends on the internet, what TV packages are most popular and what phone plans are most commonly used helps us in creating representative conclusions in our communities. This information helps us see and understand your preferences, in turn, helping us create better products and services that cater specifically to you. Through TELUS Insights, we can easily receive, organize and interpret de-identified data to help with your personal and business needs.
Threats Around Big Data
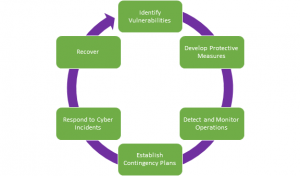
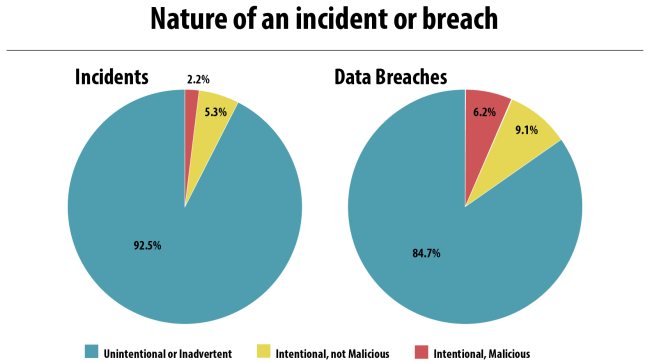
With big data, comes a bigger risk of managing, sharing, and protecting private data. Here are two main threats that stem from big data:
- Data Privacy – Storing data on a network is a threat many businesses, or online uses take. Maintaining data may seem very simple and intuitive. In reality, it is the biggest threat in modern day businesses. We make sure that the data we receive from our customers are fully de-identified, meaning nothing can be traced back to the original user. TELUS Insights is fully protected in real time.
- Incompetent Analytics and Poor Data Management – Big data is very hard to organize, navigate and interpret. All sorts of data come piling into our database in real time every day and it could be hard to manage. With TELUS’ Geo-Intelligence and Custom Data Programs, we can easily organize and extract specific data we need, when we need it.
Understanding the implications and risks behind companies that hold large data, we can conclude that “customer loyalty is our industry’s ultimate battleground”, (TELUS, 2018). We understand the risk. Knowing this, our team will continue to listen to our customers and innovating, so you guys are happy with our service.