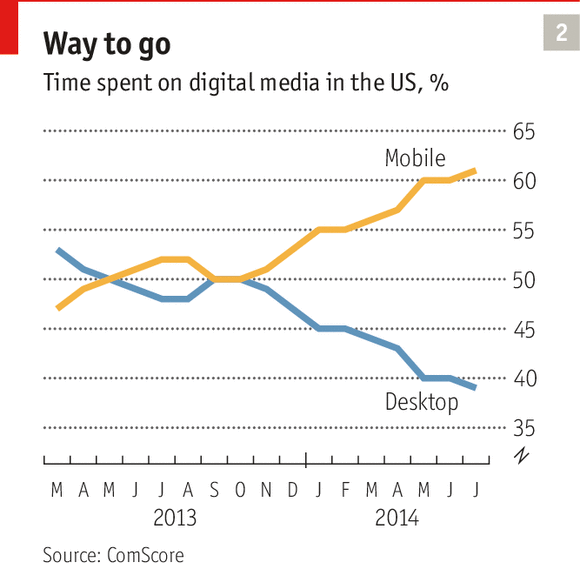
From computer to mobile
First we need to acknowledge a new trend: Internet users spend more and more time on their phones when surfing the web at the expense of their computers. That turning point happened in the fall of 2013 in the United States and is expected to happen in 2015 in the United Kingdom according to an article in the Economist issue of September 13th, 2014.
This means a whole different strategy for media content providers. The devices are smaller, and consequently the size of the screen, and the consumers have less patience than when they are browsing over their computer.
Therefore digital strategies need to evolve along these new lines when advertising in order not to antagonize users. Indeed 144 million people worldwide uploaded to their browser an adblock module that hides ads on computers according to the 2014 Adobe report.
There are at least two ways to go under the radar of web users: camouflage and targeting.
Camouflage
The idea for companies is to try and merge their advertising into the rest of the web. Native advertising tries to be less intrusive that classic banners and posters. Baby banners, for instance on the Angry Birds app, tend to take too much space and do not offer a great return considering that it takes a lot of space on mobile screen and that users feel trapped when they accidentally click on the link. The same “trapped” feeling arises when a commercial takes too long before you can click on”skip” on YouTube.
Camouflage on social media
On Facebook for instance,ads appear discretely on the side column or on the main newsfeed as recommendations based on the former clicks of the users. But the strength of social media is to make the users feel that they are the ones deciding what ads they want to look at. On a voluntarily basis users “like” pages of companies or “share” updates and “follow” companies and “retweet” their posts. That is the strength of social media and companies just need to be where the eyeballs of their customers are.
Camouflage through SEO
We could argue that it is no longer camouflage as to a certain extent everybody knows how the referencing system works on a web browser like Google works. The end goal is to arrive first on the result page of as many research keywords’ combinations. There are tricks to get to the top (the way the website is linked to others and the way it is built for instance), and there is also classic ad space that can be purchase to rank first and that are tagged with a yellow “advert”.
A new trend is appearing: inner referencing. People looking for a restaurant in San Francisco might as well type in their search engine “10 best restaurant in San Francisco” and let Google do its magic (after all we are all lazy). The results of such a search provides insights from established travel guides or newspapers… as well as websites dedicated to making rankings, on which companies pay to be ranked. A referencing site within Google’s referencing: the new Russian nesting doll.
Targeting
Geofencing
The location capability of mobile phones is an interesting feature for advertisers as they can keep track of their targeted market segment. For instance Pantene and the Weather Channel send relevant ads to customers depending on the current weather in their postal area or flower shops sending ads to customers within driving distance. This can be a dangerous game for these firms though. If the targeted customers realize how they have been played and how far the technology can go, they can have a negative reaction, feeling that these companies are invading their privacy too much.
Behavioral targeting
The idea in online advertising is not to target to the masses as a billboard in the street would, but to select a certain type of customers and target them thanks to a list of characteristics. Advertisers can thus hit the target more precisely and generate more revenue for their client. This is made possible by the amount of data that is collected thanks to cookies (see other post), web users now leave a trail of information behind them. A classic example would be the follow up email received the day after by customer having searched for certain products on an ebusiness website without yet purchasing it. Depending on people it will be perceived as either intrusive or considerate and convenient.
In a nutshell…
We thought watching the series “Mad men” had given us all the keys to advertising agencies… and yet this era seems to be centuries old. Advertising has taken the path of technology and we are not sure yet what will be the consequences. Finance took that turn decades ago and advertising is following today. Buying advertising space is made through programmatic bidding: computers enter a bidding competition after being programmed to purchase a given space thanks to the characteristics of a targeted group.
Hopefully the system will not derail as the finance did…
Source: the Economist special report “Advertising and technology”, September 13th 2014.