Introduction:
The objective of Assignment 1:3 is to gain insight in differentiating between the levels of details of definitions and selecting the right level of detail for a definition depending on the situation. Furthermore, by practicing in defining a technical term to readers from a non-technical audience, we gain understanding of how audience and purpose indicate the need for definition. This assignment will allow us to learn to appreciate the importance and role of definitions in technical writing. The term I have chosen is honeypot and the scenario will be a university professor teaching high school students about network security.
Term: Honeypot
Parenthetical definition:
A honeypot (a trap) is computer security system used to lure hackers into attacking it.
Sentence definition:
A honeypot is a computer security system designed to attract, detect and deflect hackers that attempt to hack it.
Expanded definition:
Etymology:
The term honeypot originates from the analogy where a bear is distracted by honey put as bait by hunters (Spacey, 2017).
Operating Principles:
The key principle when designing a honeypot is to consider the nature and purpose of the honeypot. Depending on the purpose of the honeypot, the honeypot can either be passive or aggressive towards hackers. Normally, honeypots that are used for protecting the server will be passive and honeypots that are used for research are more aggressive in nature where it is actively searching for an attack (Ng, Pan & Xiang, 2018).
Required Conditions:
In order for a system to be called a honeypot, the system must intentionally contain vulnerabilities. Vulnerabilities are flaws or weaknesses in a system where hackers can exploit them and manipulate the system however they wish. In a honeypot, the vulnerabilities cannot be too obvious or contain too many of them or hackers will not attack it.
Example:
An example of a honeypot would be a copy of a e-commerce site. An e-commerce site typically would hold a database filled with credit card information. This site would be poorly secured in order to attract hackers. In place of the real database would be a database filled with bogus information.
History:
The term honeypot was first used to label a spying technique in the Cold War (Joshi & Sardana, 2011). However, in the technology world, the term honeypot was first used in Clifford Stoll’s “The Cuckoos Egg” and Bill Chewick’s “An evening with Breford” in 1991 (Joshi & Sardana, 2011). The two publications describe how hackers were caught using honeypots. In 1997, the first honeypot system, “The Deceptive Toolkit” developed by Fred Cohen, was released (Joshi & Sardana, 2011). The toolkit intentionally had many vulnerabilities to trap hackers that were attracted to it (Ng et al., 2018). It is now deemed the original and landmark of honeypots (Joshi & Sardana, 2011). In 1998, the first commercial for a honeypot system, CyberCop sting3 was promoted (Joshi & Sardana, 2011). With the introduction of honeypots in commercials, honeypots began to garner much attention. In 2002, the Honeynet Research Alliance was founded and composed of people around the globe sharing their honeypot research (Joshi & Sardana, 2011). This allowed for honeypots to be used around the globe. Although honeypots are used to lure and trap hackers, they were intentionally made for educational purposes where they could analyze the attacking methods of hackers (Ng et al., 2018).
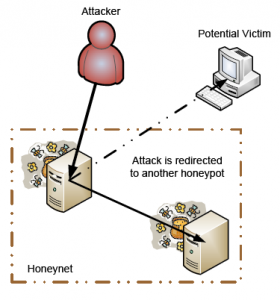
Figure 1 Honeynet
In Figure 1, the attacker is being redirected from one honeypot to another because it fell into the trap of a honeynet which is two or more honeypots (Peter & Schiller, 2008). A honeynet has the same function as a honeypot. Due to the increase in honeypots in a honeynet, the hacker is prolonged even further from attacking the real system. During this time, the hacker’s attacks can be observed and studied (Peter & Schiller, 2008).
Works Cited:
Joshi, R. C., Sardana, A. (2011). Honeypots: A new paradigm to information security (1st ed.). Enfield, N.H: Science Publishers. doi:10.1201/b10738
NG, C. K., Pan, L., Xiang, Y. (2018). Honeypot frameworks and their applications: A new framework (1st 2018 ed.). Singapore: Springer Singapore. doi:10.1007/978-981-10-7739-5
Peter, E. & Schiller, T. (2008). A Practical Guide to Honeypots. Retrieved 2019, Sep 23, from https://www.cse.wustl.edu/~jain/cse571-09/ftp/honey/
Spacey, J. (2017, March 8). 11 Examples of a Honeypot. Retrieved 2019, Sep 23, from https://simplicable.com/new/honeypot
Leave a Reply