Video: “CNET Update – Lenovo poisoned its own PCs with Superfish adware” uploaded by CNET
Have you, or someone you know, purchased a Lenovo computer lately? Over the past few days, Lenovo has been making the news due to the recently discovered adware the company has been pre-installing onto their Windows machines. Adware is a type of software that automatically produces ads or changes search results to include ads or sponsored websites. Examples of this are the ads that appear on a person’s Facebook news feed, and the ads that appear as the top results of a Google search. The point of adware is to earn extra revenue by having users click on the ads or the advertised company sponsoring the company displaying the ads. This is exactly what Lenovo did.
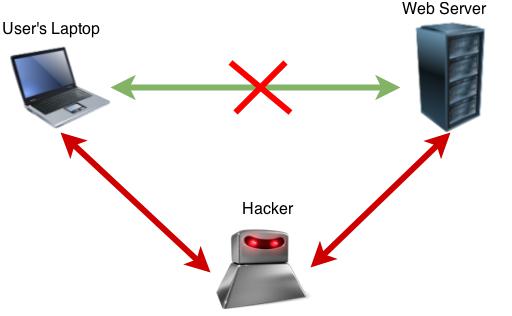
Lenovo thought they could earn a bit of extra cash by pre-installing an adware called Superfish Visual Discovery on computers that were shipped out between October and December 2014. Sounds annoying but harmless, doesn’t it? Not quite. It turns out Superfish is not just considered by many anti-virus programs as malware (malware is malicious software like a virus), but it is a backdoor for hackers to access your information. Superfish works by recognizing images viewed on the computer, finding items that are similar, and then intercepting all of the messages sent to and from a web server to inject pages that appear in your browser with additional information (like an ad). Usually, there is a mechanism in place on a web server, which verifies each user it speaks to, but Superfish circumvents this by creating a false certificate–a certificate is what the server uses to verify the connection–that all sites will see and accept. This means that any site, including secure ones like your bank or your Amazon account (any site that starts with https://…) is intercepted. Most people call this functionality a man-in-the-middle attack. In essence, a man-in-the-middle attack is when an entity redirects traffic to go through them. This allows the hacker to eavesdrop on, or inject information into the conversation.
Starting to sound a little scary, isn’t it? Well, another noteworthy point is that Superfish designed their software to create the same certificate for any instance of the software. This means that every computer running Superfish has the exact same certificate and encoding code. Thus, if someone were to figure out the key or “password” to the encryption, then they could hack every single computer running Superfish by having the same certificate. Suddenly, the pool of targets just got a lot bigger.
To avoid vulnerabilities, if you or someone you know has just bought a Lenovo computer, I suggest finding out if Superfish is installed by crosschecking the model of computer with the list of models that may have been affected. If Superfish is installed, follow Lenovo’s instructions to remove it. Lenovo made a huge mistake by pre-installing this adware on their products, but two software engineers, Chris Palmer and Mike Shaver, from Google and Facebook respectively, are to thank for bringing global attention to this security issue and subsequently protecting users.
Signing off,
Dorothy Ordogh