Researchers:
- Karthik Pattabiraman, Professor
- Asem Ghaleb, PhD candidate
- Rui Xi, Masters student
Problem Motivation
One of the attractive applications associated with blockchain technology is the decentralized applications (DApps) called smart contracts. Smart contracts are programs deployed and running on the blockchain that are executed autonomously. Smart contracts are used for cases such as financial services, credit enforcement, supply chain, digital identity, etc. The financial nature of most smart contracts provides an incentive for attackers to find bugs in the code of the contracts to exploit and steal money. The past few years witnessed several attack incidents that targeted smart contracts and led to the loss of millions from the targeted smart contracts. This project aims to expand the space of bug detection by proposing systematic approaches for evaluating the efficacy of smart contract analysis tools and building techniques for effective detection of bugs and violation of community guidelines. We mainly build techniques that automatically analyze the code of the smart contracts to be used by developers for writing secure and reliable smart contracts.
Approach
In this project, our proposed approaches are based on the use of program analysis techniques, mainly static and dynamic analysis. We have proposed a systematic approach for evaluating bug-finding tools by injecting bugs in the code of smart contracts based on the static analysis of the code. Further, we are working on proposing a static analysis approach for detecting vulnerabilities in smart contracts by tracking data-flows in the code of smart contracts. We are also working on building an approach for analyzing how large the gap between community guidelines and the developers’ practice is for using low-level functions.
Results
- Asem Ghaleb and Karthik Pattabiraman. How Effective are Smart Contract Static Analysis Tools ? Evaluating Smart Contract Static Analysis Tools Using Bug Injection. Proceedings of the ACM SIGSOFT International Symposium on Software Testing and Analysis (ISSTA), 2020. (Acceptance Rate: 26%) [PDF | Talk] (DataSet, Code – Artifacts Functional Badge
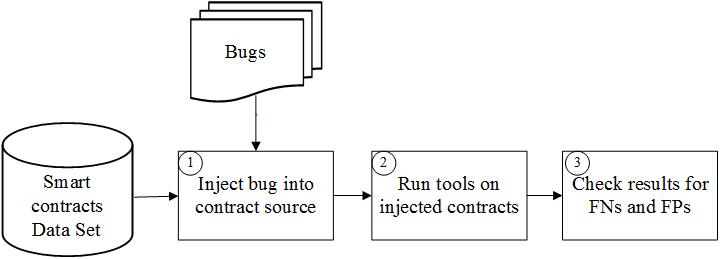
SolidiFI is a methodology for systematic evaluation of smart contracts’ static analysis tools to discover potential flaws in the tools that lead to undetected security bugs. We have used SolidiFI to evaluate six well-known static analysis tools (Oyente, Securify, Mythril, Manticore, Smartcheck, and Slither), and the results of our evaluation study showed that all of the evaluated tools have significant false-positives and false-negatives in addition to misidentifying a large number of bugs.
